Software is fragile, people make mistakes, and despite robust investments, any organization can be breached. With enough effort and the right resources, hackers will compromise assets of the most secure enterprises.
The good news is that malicious actors are focused on the low hanging fruit (and there’s a lot of it). They want to find the path of least resistance that will provide the greatest return (something we all can learn from).
The other good news is that breaches happen in stages and typically transpire over extended periods of time. The Equifax breach, for example, started with an unpatched web portal vulnerability and was propagated by misconfigurations in segmentation that allowed access to passwords in plain text. The login credentials allowed the hackers to access further systems and steal data from the network by exploiting an expired encryption certificate, yet another easy-to-fix security issue.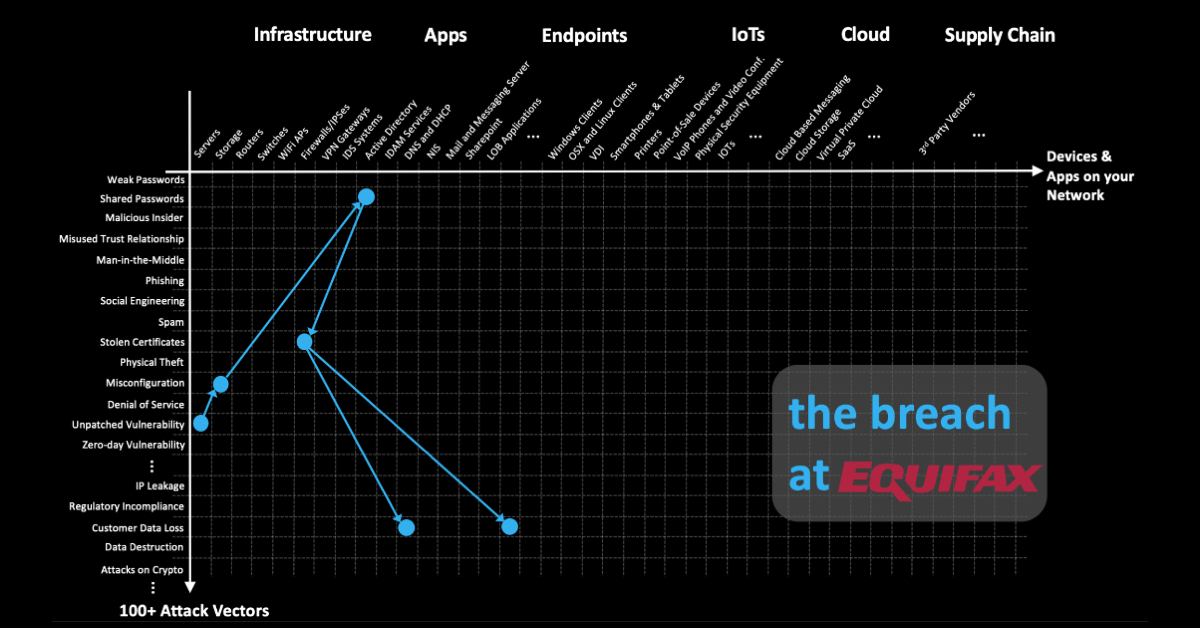
If Equifax had fixed even one or two of the security issues prior to the breach, it is possible that the attack could’ve been stalled and the severity mitigated. By staying on top of all vulnerabilities and proactively mitigating risks, organizations can ensure that adversaries do not have the time or resources to successfully carry out each stage of a breach and ultimately exfiltrate sensitive data from their systems. This is at the core of becoming cyber resilient.
Building cyber resilience starts with understanding how breaches happen and the defenses you can set up to make each stage more debilitating for the adversary. Here are the 4 stages of a breach:
1. Perimeter Compromised
Your extended perimeter includes all enterprise assets that are in direct contact with the internet. This includes firewalls, public web servers, VPN gateways, mobile devices, IoTs, every device that receives external messages or is used to browse the web, and third parties with access to the company’s network or data.
Some of the biggest breaches in recent history started with a minor breach in the perimeter. A vulnerability in an application firewall protecting an AWS account led to Capital One’s loss of over 100 million customer records last year. For Target, it was a successful phishing campaign on their HVAC vendor that provided adversaries a foothold into their target systems (no pun intended).
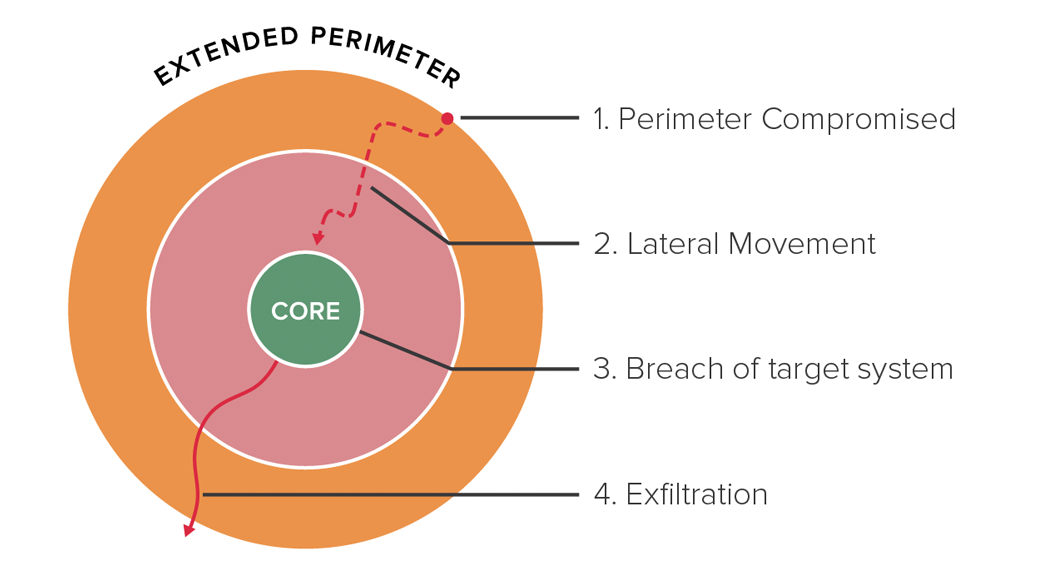
2.Lateral Movement
After breaching the perimeter, attackers use various techniques to move inwards and sideways inside your intranet to gain access to additional systems. This is typically easier than the initial breach because companies optimize their internal access control policies and protocols for ease of collaboration and not for cybersecurity.
After hackers compromised Uber’s private GitHub repository in 2017, they were able to hastily unearth login credentials for an Uber AWS account that stored personal information on nearly 58 million drivers and riders.
3. Breach of Target System(s)
Once the hacker reaches their target asset, they are presented with a few options: steal data, destroy data, impair the system, or just lie in wait. For Uber, the hackers decided to steal the data and demand $100,000 from Uber to destroy it, instead of selling it on the dark web.
The target system for Target’s hackers was the retailer’s Point of Sale (POS) systems, also known as cash registers. Data-stealing malware was installed on a majority of the Target’s POS systems and in just 18 days, about 40 million customer debit and credit cards were compromised.
4. Exfiltration
The last step of a successful data breach is transferring the targeted information to a system outside the exploited company’s network. Although this step is not often talked about, it can be the most difficult. Among the methods of exfiltration are backdoors with built-in download functions, FTPs not protected by firewall, and setting up forwarding rules in email.
Breach Likelihood vs. Effort by Adversary
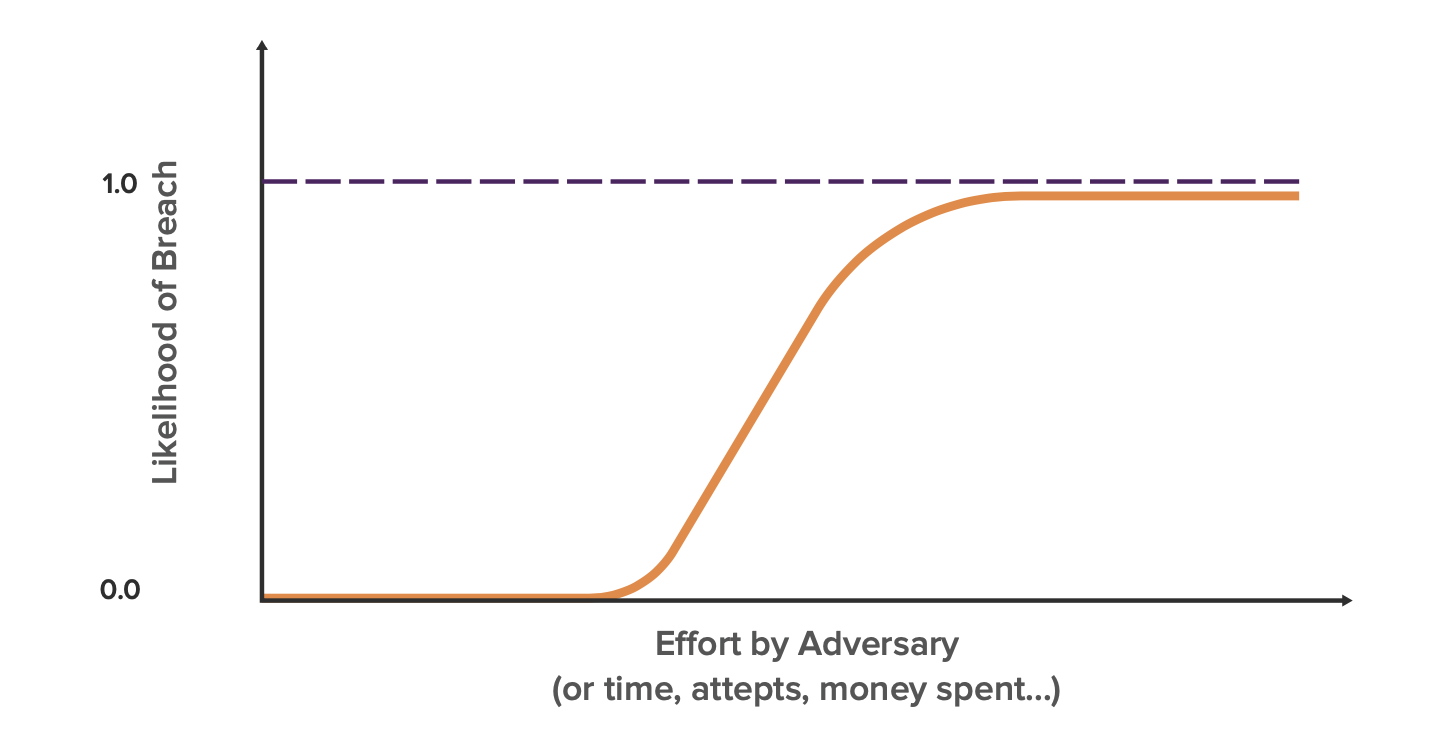 Each of the 4 stages of a breach require varying levels of effort, depending on the security controls and infrastructure of the organization under attack. In the next blog on Understanding Cyber Resilience, we’ll look at key factors affecting how cumbersome these stages are for the adversary and preventative measures that can be taken to decrease the likelihood of each stage being completed.
Each of the 4 stages of a breach require varying levels of effort, depending on the security controls and infrastructure of the organization under attack. In the next blog on Understanding Cyber Resilience, we’ll look at key factors affecting how cumbersome these stages are for the adversary and preventative measures that can be taken to decrease the likelihood of each stage being completed.


