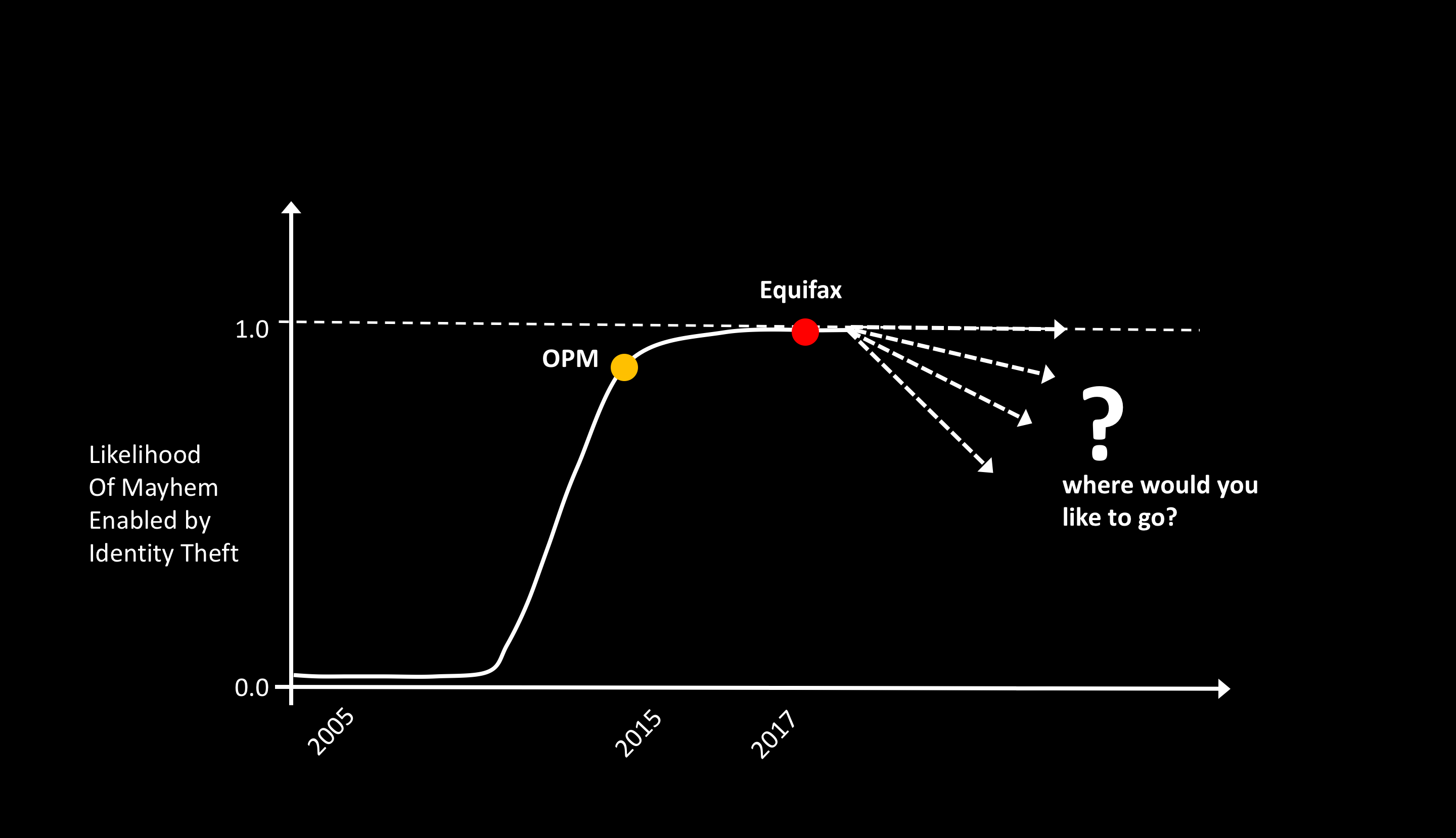
In recent days, there have been a lot of coverage of the Equifax breach. There is criticism on how Equifax is handling the breach, reports on how Equifax executives sold company stock after learning about the breach, explanations and rebuffs on how the breach happened, posts on the reality of lifelong identity theft, and tips on how consumers can protect their identity. Avivah Litan of Gartner has written a great piece on the overall fallout from this breach, and new dynamic identity data technology that organizations should adopt.
This post is about what you as an employee of a business can do, post-Equifax, about stopping identity theft, and an opportunity for three big tech companies—Google, Apple and Microsoft.
On the first topic: do you work for an institution that is in the business of money (banks, insurance, the IRS), or information (credit agencies, mortgage brokers, etc.). Are you a person who decides if an account gets opened for someone, or if they get a loan or a payment? You could also be a CISO or executive whose job is to set policy about digital risk. Maybe you are a software developer working on the authentication module of a web site.
Here are some specific things you can start do today to greatly reduce the likelihood of identity theft in your domain. And, it does not really matter if your company has been breached, or not, this stuff is still relevant.
- Assume things are not what they seem to be
During the course of your day, when someone presents or submits personal information (or some other authentication information, like a password) to establish their identity, you must assume that the information being presented might be stolen. You must also assume that the information in the report that you pulled about this individual from one of the credit agencies has also been stolen. Given recent breaches, the likelihood of this is pretty close to one. Your goal is to take steps to efficiently distinguish between the normal honest use case, and the fraudulent use case.
- Think physical
Insist on secondary forms of identity verification, something physical. Sure, maybe they stole personal information, but it is much harder for a cyber-criminal to ALSO steal or reproduce physical personal stuff, such as access to a phone or the physical residence of the individual. Note that knowing the phone number or address of an identity is not key– it is demonstrating actual physical access.
If your interaction with the individual is in the physical world, an original driver’s license, original passport, can be one of the physical factors you insist on. If you are not completely satisfied with the government issued ID – maybe the picture does not match well or the ID looks flakey, think – do they have access to additional physical “something” which matches up with the information in their credit report or the other information they are presenting. This could be an ATM card and a credit card with their name on it that they have in their possession, and which actually works. Ask them if they have their cell phone bill on them, match the account number with the credit report, and then actually call their cell phone. Remember, that you are chaining multiple physical factors of authentication, and trying to get comfortable with the likelihood that ALL the factors in the chain have not been compromised.
If your interaction with the individual is remote, i.e., over the phone or the Internet, you must continue to think physical. If you have good reason to believe you know the correct phone number of this individual (previously established 2-factor authentication, information in credit information or other public record), call or text the number and ask them to confirm if they are currently engaged in the activity or transaction you are trying to verify. (Make sure your question is a simple Yes/No question – it must not itself appear as a phishing attempt.) Obviously, a new or different phone number provided by the individual as part of the transaction, that has no concordance with past information does not count as a valid physical factor.
If you do not have a good phone number to work with for physical authentication, you have two choices. Go to snail mail – send a verification letter to a physical address that you have good reasons to believe is the correct address. Alternately, you can work with partners. For example, you can establish direct relationships with reputable phone companies or banks that will give you a current phone number associated with a particular physical address. Or you can work with a trusted partner who your customer/prospect has to physically present themselves to, and verify their identity. After physical verification, use the opportunity to establish a valid phone number for this identity.
It is critically important to think physical in establishing identity, given the extent of recent data breaches. Moving by default to physically rooted dynamic multi-factor authentication is absolutely possible to implement today. In the long run, this will minimize risk for your employer. Moreover, it is the right thing to do for consumers.
Some people will tell you that there are ways to forge physical documents, or to easily obtain copies of documents like birth certificates and present them to establish a fake physical identity. All true! But the point of this post and cyber-security in general is not to solve security problems, but only to make the dynamics as risky for the adversary as they are in the physical world. If scammers have to obtain fake birth certificates to phish you, the cyber aspect of the problem has been managed. Thinking physical works.
This brings me to the second topic I wanted to talk about. This is an opportunity for Google, Apple and Microsoft, who together control almost of the endpoints – smartphones, tablets and computers – that people in America use. The opportunity for these companies is to establish a common strong identity verification platform that provides other organizations and individuals with secure and efficient ID proof services, such as the mapping from physical home address to valid phone number, or more generally from some subset of personal information to verified strong identity.
We all carry one or more of these companies’ physical technology on our person at most times. These companies know how much time we actually spend at various physical locations, what phone numbers we physically have access to, what businesses send us bills and communication. These companies’ devices can reasonably securely capture our finger-prints, faces, voice prints and other biometric information. This corpus of physical information gets continuously updated as we live our lives. These companies therefore have have higher quality physically rooted dynamic identity information about us than anyone else. The opportunity is to give people convenient real-time control over their identities, right from their devices.
It is important that this common identify platform be backed collectively between the big three, at-least in in its core service and user interfaces, so we can get universal adoption quickly. If a capable password manager, such as 1password, can be uniformly incorporated by just these three companies on the smartphone, tablet and the desktop/laptop—that will be the beginning of the end of our troubles with passwords.
There are many areas of cyber-security and risk other than identity, but perhaps none is as foundational. In the past, privacy concerns and general apathy have prevented progress on strong identity in the US. With recent breaches, Equifax and OPM, it should be clear that there is no privacy left anymore. As Avivah Litan puts it so well, our country has been hijacked! And it is now time to get it back!
