
You probably hear the terms “Security Analytics” and “AI Based Security” thrown around a lot these days. Have you ever wondered how these two are different, if at all? You might be leery of the hype around the word AI, and might have seen excellent writeups such as this on how the term AI has been hijacked by some marketeers.
Some definition review first…
Analytics is the discovery, interpretation, and communication of meaningful patterns in data. [Wikipedia]. Ergo, Security analytics is the study of security data.
Artificial Intelligence: Intelligence exhibited by a device where it perceives its environment and takes actions that maximize its chance of success at some goal [Wikipedia].
As we all know, technology generally follows an evolution. The 1903 Wright Flyer had a very simple design and flew for just 12 seconds and covered 120 feet during its first flight. A few decades later we “flew” to the moon and back, travelling over 953 thousand miles. If you were to put flight technology on a spectrum of evolution, you will have the Wright Flyer on one end and modern-day spacecraft at the other end.
Similarly, there is a spectrum of analytics maturity with security analytics at one end and AI based security at the other end. What is making us dizzy is that this timeline of evolution for analytics has been compressed into several years instead of half a century.
The outcomes generated by 1st gen security analytics tend to be focused on better understanding “what happened?” in the context of security attacks, while cutting-edge AI based approaches focus on getting ahead of the problem – i.e., “what can happen?” and “what should I do?”.
Gartner defines these approaches as “Descriptive” vs. “Predictive/Prescriptive”.
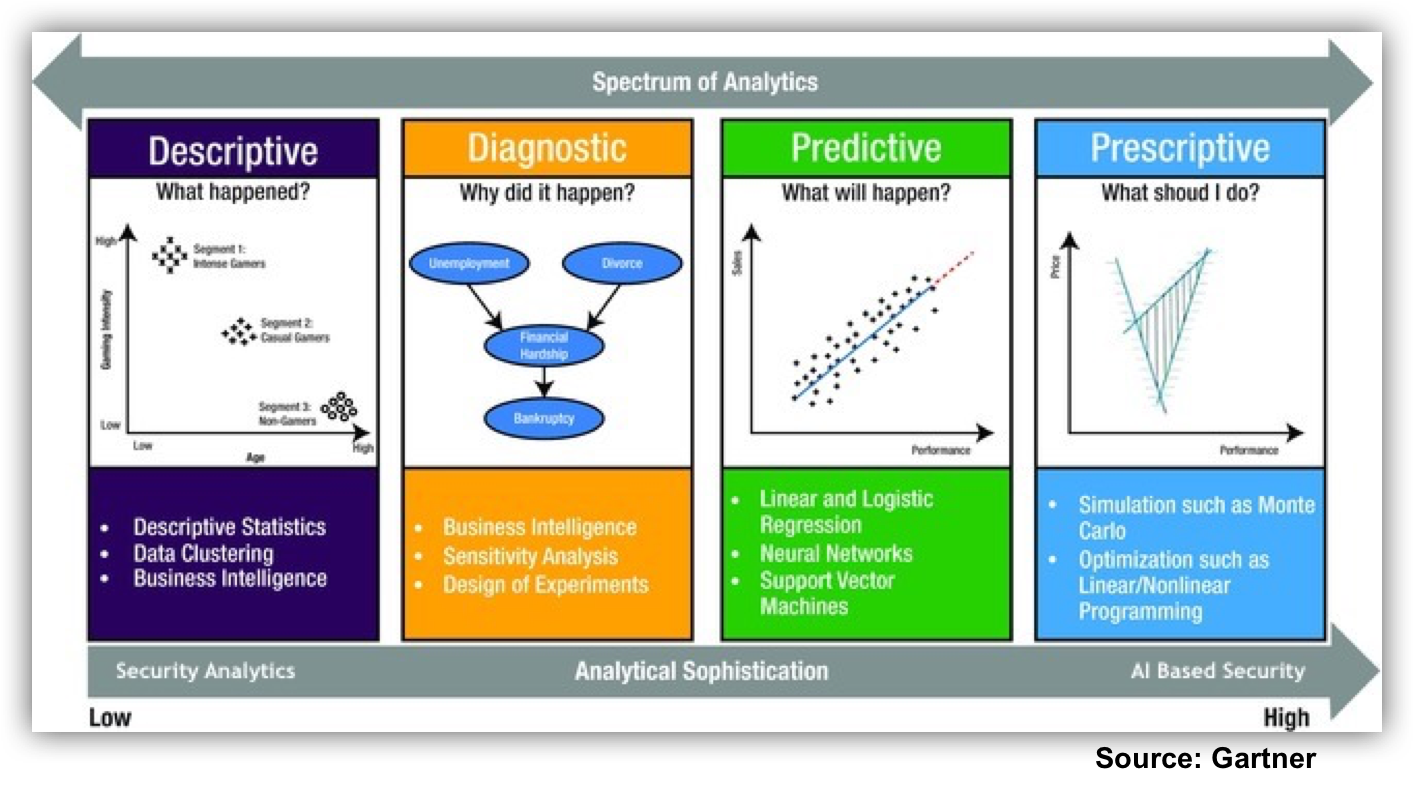
Descriptive security analytics uses data clustering algorithms that analyze properties of the entities on a network and their relationships. It uses deterministic, rules based math to do root cause analysis. There is also the BI-fication of security that sits firmly in the descriptive analytics camp. Some characteristics of descriptive analytics in the context of security are:
- Automatic math calculations, mostly around short horizon baselines with standard deviations looking for outliers
- Rules need to be updated manually as environment changes
- Backward looking, i.e., based on events that have already happened
- Ridden with false positives
- “Right of boom”, i.e., after compromise, or at the point of attack
If you were at Jonathan Care’s talk on the state of security monitoring and analytics at the recent Gartner Security and Risk Summit in June 2017, it is worth noting that security analytics, as widely implemented in the security industry, is just about to reach past the point of diagnostics in its outcomes.
However, there is a handful of companies and individuals that are using advanced AI on a select set of usecases to explore what might ultimately be correctly referred to as AI based security analytics.
So what are the properties and goals of this aspirational next step of security analytics technology? The latest AI based security approaches use lots of data science, advanced statistical methods, and self-learning techniques (e.g., Neural Networks, Bayesian Algorithms, Reinforcement Learning) to come up with a much better understanding of your security posture. Some other characteristics are:
- Almost completely automatic; we only need to train the models
- The system generally does not need to be updated manually with changes in the operating environment
- Risk focused (priority re. business impact)
- Predictive as opposed to reactive
- Continuous
- Prescriptive – analytics have internal state to walk backwards from security risk score/color to drivers
- “Left of boom”, i.e., ahead of the problem, before security breaches happen
All-in-all, the best AI based security systems tend to be context-aware, self-learning, better able to deal with incomplete data, ergo, have the potential to be smarter than traditional algorithms for security analytics. Perhaps most importantly, some of these AI based security systems have the capability to predict what can go wrong in your network, before an event happens, and surface what you should focus on fixing to avoid a security incident.
Now, advanced systems based on complex Math can be forbidding to the user. However, systems that actually bring about a leap-ahead in technology evolution, go to great lengths to abstract away the increased internal sophistication and complexity from the user. For example, when you get on a jetliner to fly from SFO to BOS, the pilot of your plane has a fairly sophisticated and highly automated set of controls, and usually does not need to worry about the hundreds of thousands of moving parts on the plane that will work together to fly you across the country. Powerful visualization is necessary to make AI based security systems usable by security operations teams and by business leaders.
Our mission at Balbix is to provide you with a security platform that helps you get ahead of the security problems arising from the hyper-dimensional attack surface of your enterprise while not having to worry about intricacies of AI/ML.
It’s time to get on-board!
