Another breach, this time of a top cyber-advisory firm, Deloitte. So the Equifax breach was about the company’s culture, and a cascade of mistakes which could have been avoided. But Deloitte is supposedly a sophisticated cyber organization in Cyber.
How did this happen? What can I learn?
Here are a few things:
- Passwords remain the most common way to breach an enterprise. It appears that at least one step of the Deloitte breach involved an administrative password. It also appears that some of the high-value information compromised were security architecture details of Deloitte’s clients, along with passwords for their clients’ systems. If everyone in the world had 2-factor authentication turned on, this would not have been a big deal.
- The adversary is going after the back door of the enterprise. These are your trusted third parties—law firms, financial and other consultants, key product vendors. Their networks might be less well defended and perhaps the easiest way into your organization.
- There is a significant gap in what standards and best practices dictate, and what actually gets implemented on the ground— this is the gap between paper risk and actual on-network breach risk. Enterprises need to invest in tools that bridge this gap, i.e., ensure that the intended mitigations and controls are actually working.
- Each CEO and Board Member must ask — what is the point of paying millions of dollars for cyber-security advise to firms like Deloitte? You need to ask for your auditors and consultants to get closer to ground truth.
The C-suite must absolutely insist on comprehensive and continuous measurement of the risk and resilience posture of an enterprise. Your breach risk roughly looks like the picture below (inspired by a diagram in Alex Stamos’s recent Blackhat talk).
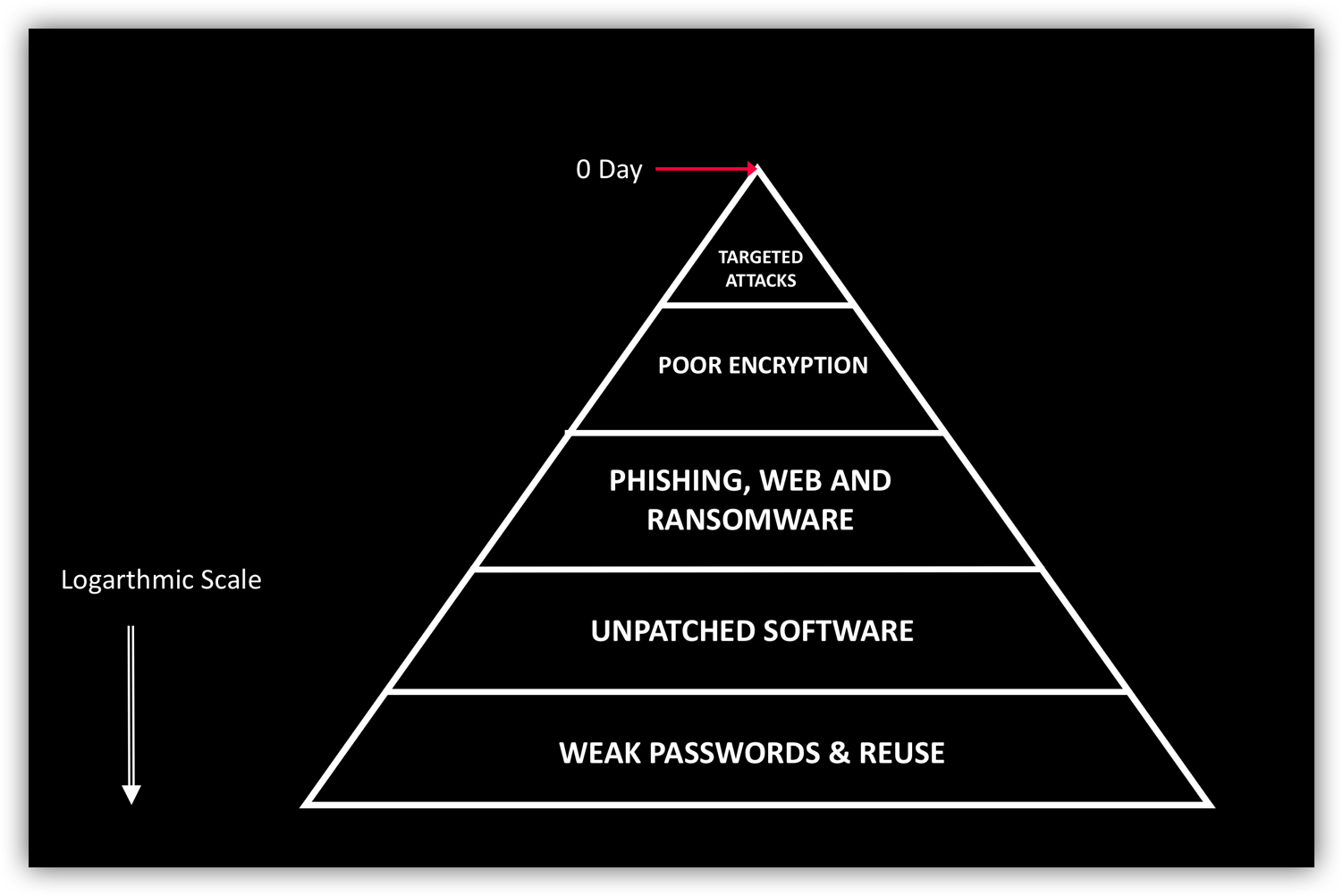 *picture inspired by Alex Stamos
*picture inspired by Alex Stamos
Your leadership team must understand the ground reality of this pyramid for your enterprise, and it must be a part of your culture to strive to improve this. AI can help surface relevant information for all stakeholders in your organization.
Ask for a continuous and comprehensive machine measured score of passwords, unpatched software, phishing and encryption, for each asset in your enterprise. This heat map must be forward looking, not based on the past. The fact that no incident has happened in the past quite a determinant of what can happen in the future. Discuss this heatmap in your e-staff meetings at some frequency, ensure all groups in the company are aware of these scores, and the shared company objectives around improving.
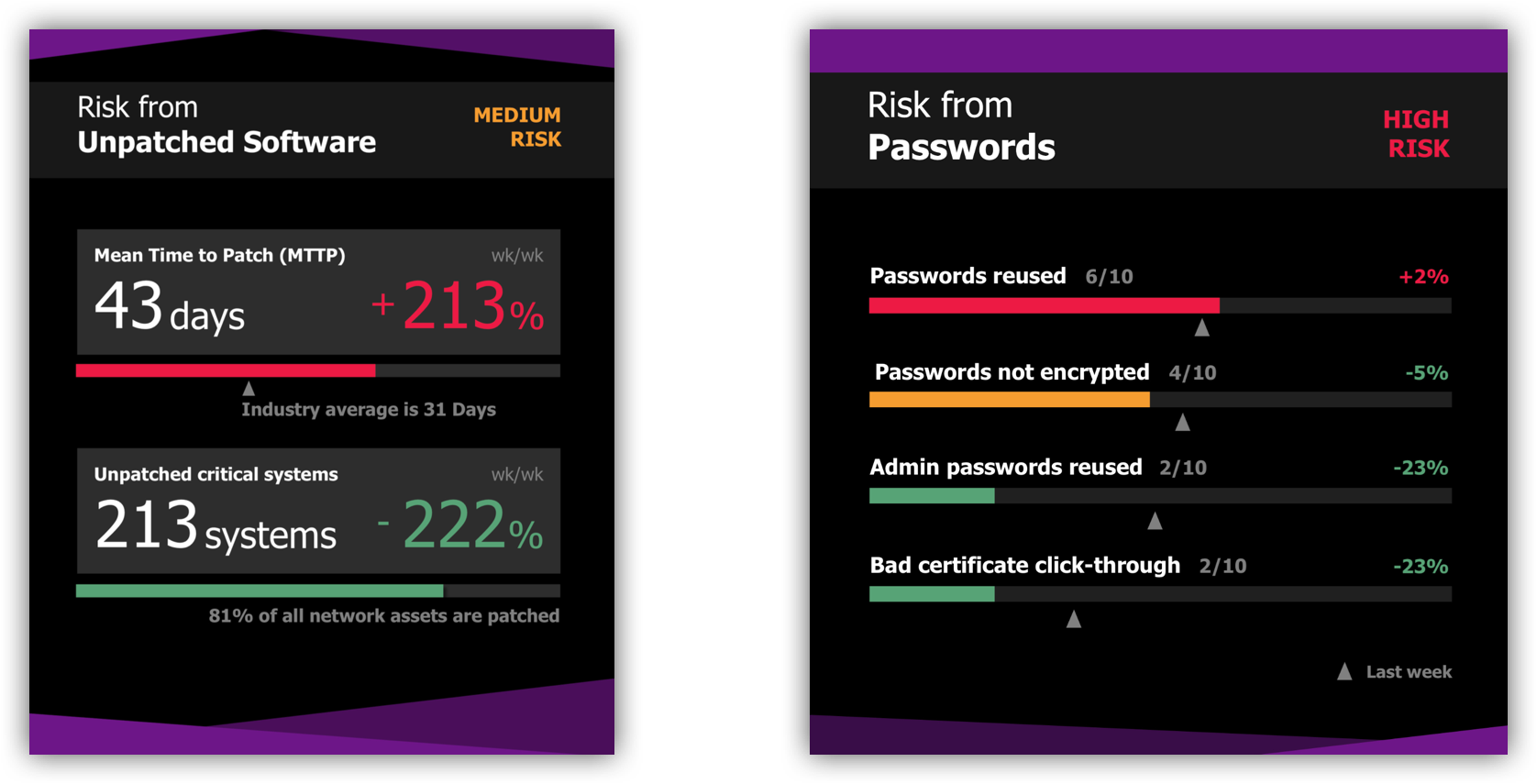
Ask your consultants and your security team for prescriptions on how to make this heatmap greener. (Balbix is happy to help you on this.) These prescribed mitigations must be scalable and practical solutions. Don’t ignore them by burying your head in the sand, even ostriches don’t!
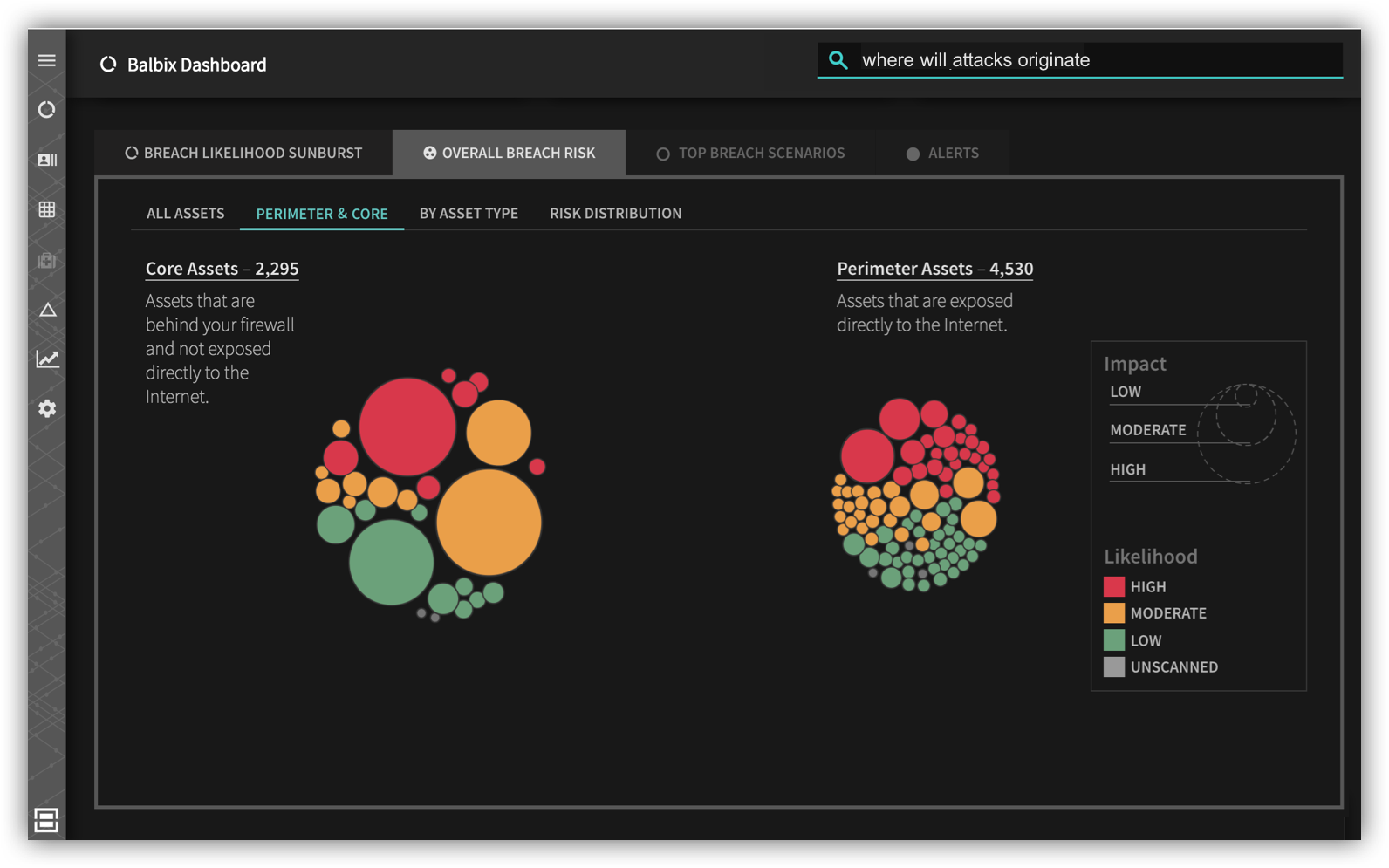
Ultimately, organizations need to focus on resilience. By now you must understand that something in your environment — some piece of software or a user— will get compromised routinely. The question is: how well will your defenses keep this incident from spreading across your enterprise. Mitigations like 2-factor authentication, application and browser isolation, next-gen endpoint controls, bastion hosts and network segmentation really help here.

Your organization must simulate these scenarios, look at the effectiveness of your mitigations and ask if you are satisfied with the results. Otherwise, Deloitte and Equifax-like cyber-disaster are inevitable.
